The Internet Archive was breached again, this time on their Zendesk email support platform after repeated warnings that threat actors had stolen exposed GitLab authentication tokens.
Since last night, BleepingComputer has received numerous messages from people who have received responses to their old Internet Archive takedown requests, warning that the organization has been breached for not properly rotating their stolen authentication tokens.
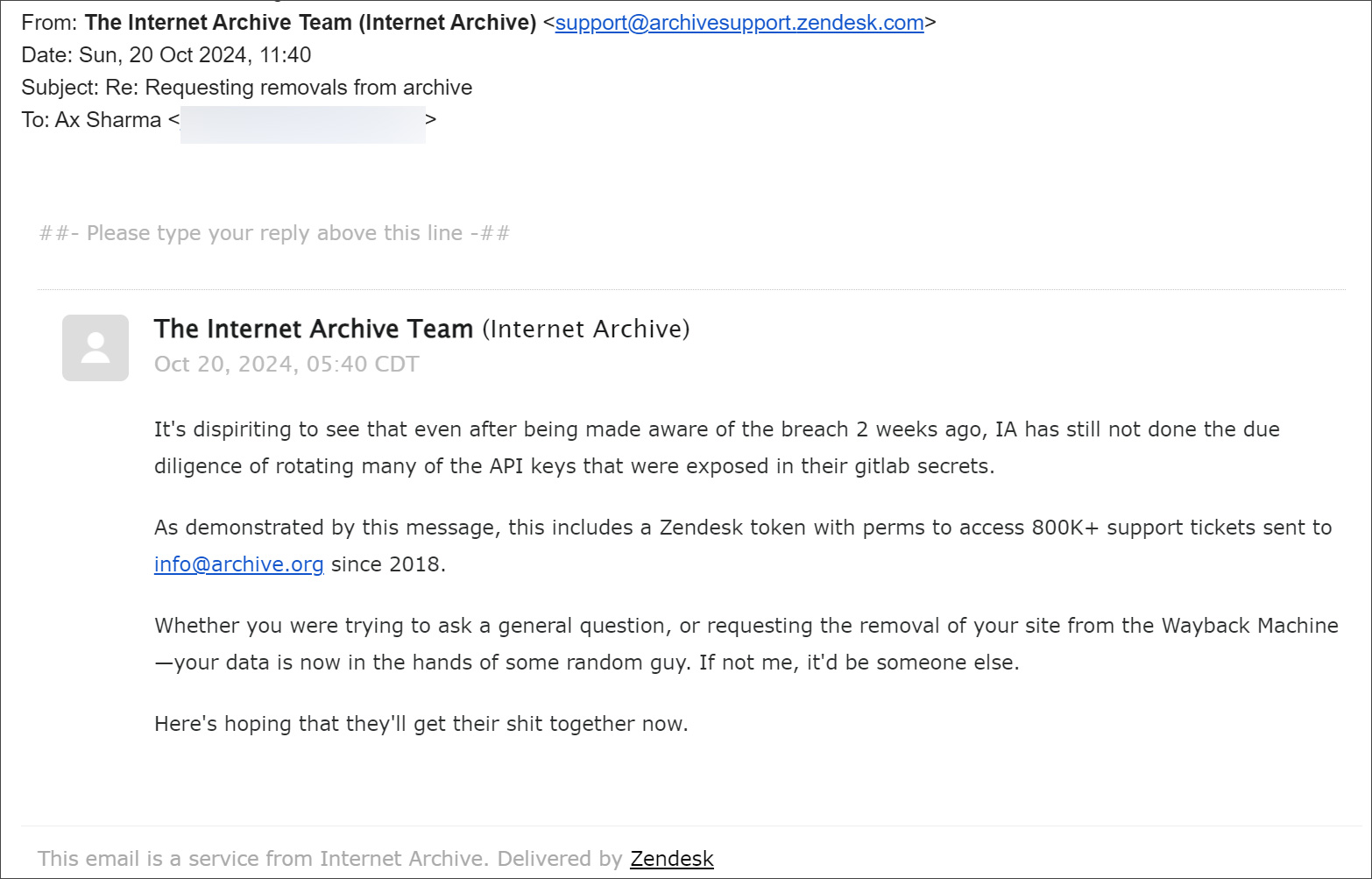
“It is disheartening to see that even after being notified of the breach weeks ago, IA has still not done due diligence in rotating many of the API keys exposed in their Gitlab secrets ” reads an email from the threat actor.
“As this message shows, this includes a Zendesk token with permissions to access over 800,000 support tickets sent to info@archive.org since 2018.”
“Whether you were trying to ask a general question or requesting your site’s removal from the Wayback Machine, your information is now in the hands of some random guy. If it wasn’t me, it would be someone else.”
Source: BleepingComputer
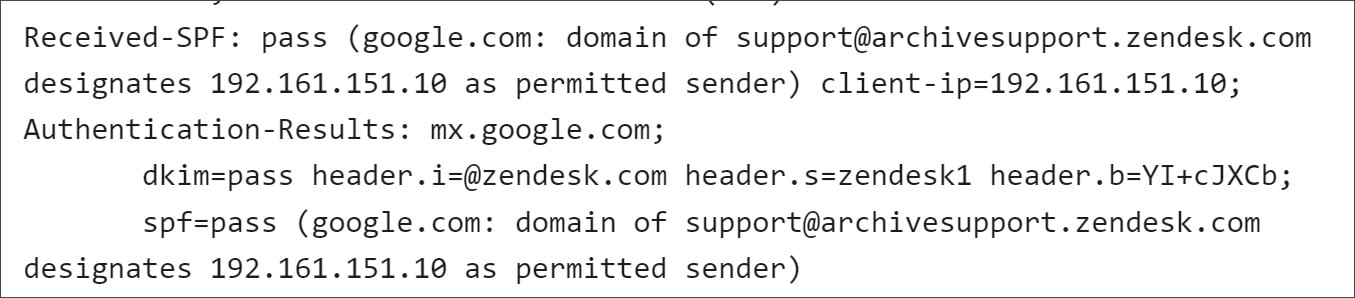
The email headers in these emails also pass all DKIM, DMARC, and SPF authentication checks, proving that they were sent from an authorized Zendesk server at 192.161.151.10.
Source: BleepingComputer
These emails come after BleepingComputer repeatedly attempted to alert the Internet Archive that their source code had been stolen via a GitLab authentication token that had been online for almost two years.
Exposed GitLab authentication tokens
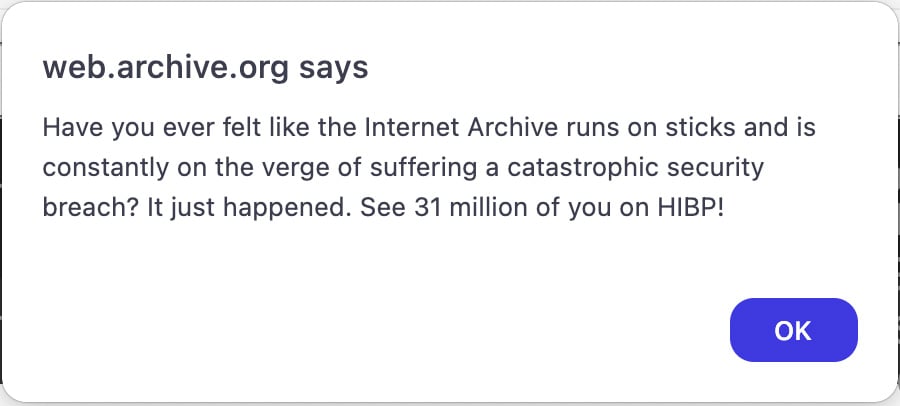
On October 9, BleepingComputer reported that Internet Archive was hit by two different attacks simultaneously last week: a data breach that stole the site’s user credentials for 33 million users and a DDoS attack by a pro-Palestinian group called SN_BlackMeta.
Although both attacks occurred during the same period, they were carried out by different threat actors. However, many media outlets incorrectly reported that SN_BlackMeta was behind the breach and not just the DDoS attacks.
Source: BleepingComputer
This misreporting frustrated the threat actor behind the actual data breach, who contacted BleepingComputer through an intermediary to take credit for the attack and explain how they had breached the Internet Archive.
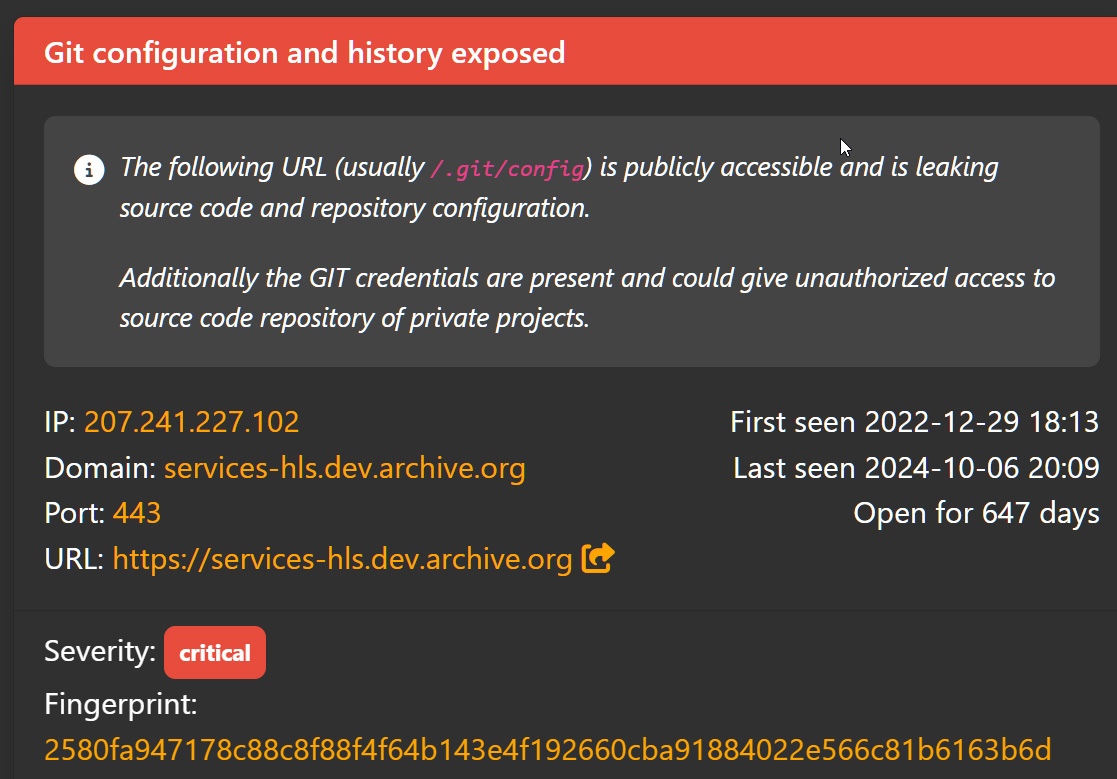
The threat actor told BleepingComputer that the first breach of Internet Archive started with finding an exposed GitLab configuration file on one of the organization’s development servers. services-hls.dev.archive.org.
BleepingComputer was able to confirm that this token has been exposed at least since December 2022 and has rotated several times since then.
Source: BleepingComputer
The threat actor says that this GitLab configuration file contained an authentication token that allowed them to download the source code from the Internet Archive.
The hacker says this source code contained additional credentials and authentication tokens, including the credentials for the Internet Archive’s database management system. This allowed the threat actor to download the organization’s user database, further extend the source code, and modify the site.
The threat actor claimed to have stolen 7TB of data from the Internet Archive, but would not share any samples as proof.
However, we now know that the stolen data also included the API access tokens for Internet Archive’s Zendesk support system.
BleepingComputer has repeatedly tried to reach the Internet Archive, most recently on Friday, offering to share what we knew about how the breach occurred and why it occurred, but we never received a response.
Lack of cyber-street cred
After the Internet Archive was breached, conspiracy theories abounded as to why they were attacked.
Some said Israel did it, the United States government, or companies in their ongoing battle with the Internet Archive over copyright infringement.
However, the Internet Archive was not breached for political or monetary reasons, but simply because the threat actor could.
There is a large community of people who trade stolen data, whether they do it for money by extorting the victim, selling it to other threat actors, or simply because they are data breach collectors.
This data is often released for free to obtain cyber street cred, increasing their reputation among other threat actors in this community as they all compete to see who has the most significant and most publicized attacks.
In the case of the Internet Archive, there was no money to be made by trying to extort the organization. However, as a well-known and extremely popular website, it has certainly boosted a person’s reputation within this community.
While no one has publicly claimed this breach, BleepingComputer was told that this happened while the threat actor was in a group chat with others, with many receiving some of the stolen data.
This database is now likely being traded among other people in the data breach community, and we’ll likely see it leaked for free on hacking forums like Breached in the future.





